Vulnerability Archive

2014 Internet Security Threat Report
Symantec has released it’s 2014 Internet Security Threat Report. This vulnerability report presents an overview and analysis of the year in global threat activity. They reached volume 19 with this threat report. The report is based on data from the Symantec Global Intelligence Network, which Symantec’s analysts

Heartbleed Hit List – Websites affected by heart bleed
As I said in an earlier post, Heartbleed, an OpenSSL vulnerability affected over half of the internet websites. Now comes the most important questions: Should I change my password? What websites were affected? The most affected websites are the social networks, the search engines and the email

Heartbleed security bug in OpenSSL affected over a half of the internet
Heartbleed bug was discovered in OpenSSL. OpenSSL is an open-source implementation of the SSL and TLS protocols. The core library is written in the C programming language. OpenSSL implements the basic cryptographic functions and provides various utility functions. This bug allows random reading of servers memory in

Snoopy drone can hack your smartphone when you’re on street
Snoopy is a distributed tracking and profiling framework. According to the British experts from Sensepost Security, the project called Snoopy demonstrates the danger of using drones without clear rules. Sensepost created a distributed tracking and data interception framework, which performs simple tracking, real-time and historical profiling of
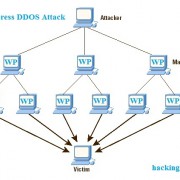
Over 162 000 WordPress Websites used to perform DDOS Attack
What is a DDOS attack? And what’s the difference between DOS and DDOS attacks? A DoS attack (Denial-of-Service) involves an attempt to disrupt operations that run a computer or network that is connected to the Internet. The most common form of DoS attack is that the operation
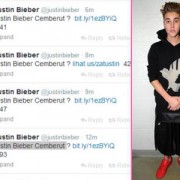
Justin Bieber’s Twitter Hacked
Pop Singer Justin Bieber’s Twitter account hacked. 50.2 million Twitter followers received a myriad of odd messages on Saturday (March 8), as Justin Bieber’s official Twitter account was hacked with links to a viral app named ShootingStarPro. Twitter account with the second most Twitter followers. Spammers tweeted in Indonesian language from his
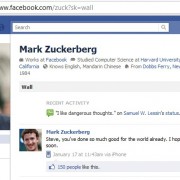
Mark Zuckerberg’s Timeline Cover Photo Hacked ?!
The hacker Dr.FarFar claimed that he changed the Timeline Cover Photo of Mark Zuckerberg’s Facebook account. Hacker Dr.FarFar explained that he used the “Report abuse” option on Zuckerberg’s Cover image, and choosed, “I don’t like this photo of me” and then “I used Fiddler2 Debugger Program to
Magento Go vulnerability allows hackers to bypass the authentication by creating administrator account
According to Securatary, this vulnerability allows for a cross store (unauthenticated, as we have not authenticated to our target store) privilege escalation attack, that will create a user on any *.gostorego.com store. There are over 200 000 active Magento Go stores. So this attack allows access to
Secret.ly App Hacked, they discovered First Security Issue
The anonymous sharing app, Secret, has been recently hacked. The hack is not so serious, it doesn’t expose who said what (maybe in the future someone will expose this too). What you can be sure about, is that nothing is anonymous on the internet (excepting the Anonymous

Telecom provider Orange hacked, 800 000 customer records stolen
According to Pc Impact, the page “My Account” was the target of an attack Thursday, January 16. The ISP states that personal data were stolen, but the passwords are not affected. Less than 3% of the France Telecom Orange customers are impacted. A complaint was filed: Hackers
