Vulnerability Archive

Uber database breach exposed 50000 drivers
Uber released a statement on Friday announcing that it suffered a data breach in 2014 that affected 50 000 Uber drivers across the United States. The Uber’s database was accessed by an unauthorized third party. Uber says that 50 000 driver partner names and driver’s license numbers

How to get $12500 from Facebook
Two days ago I posted an article about a Facebook vulnerability that allows deleting any photo. The person who discovered the vulnerability said on it’s personal blog that Facebook payed him $12500 for reporting this vulnerability. If you want to read about the vulnerability that Laxman Muthiyah

Facebook vulnerability allows deleting any photo
This vulnerability allowed (it was fixed recently) malicious users to delete any photo album available on Facebook. This exploit of the Facebook Graph API allowed hackers to delete any photo album owned by a user or a page or group from Facebook. The main utility of the

USBdriveby can take control of a computer in a few seconds
A few months ago was discovered a worrying vulnerability of standard USB which does not seem to be repaired, called BadUSB. Until now such information was only theoretical and no one has developed a software which can uses this security hole, but a well-known hacker Samy Kamkar has
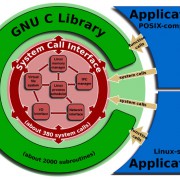
GHOST glibc vulnerability (CVE-2015-0235) affects Linux Machines
A critical vulnerability has been found in glibc, the GNU C library, that affects almost all Linux systems dating back to 2000. Attackers can use this flaw to execute code and remotely gain control of Linux machines. The Red Hat Product Security has been made aware of

IBM Study: Companies rethinking cyber security strategies
Approximately 60% of leaders in security believe that hackers have exceeded cybersecurity capabilities within their organization, said in a study conducted by IBM. Over 80% of security leaders believe that the challenges of external threats is increasing, while 60% agree that oraganizatiile are exceeded in this cyber war,
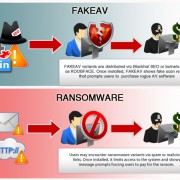
Ransomware – a malware which encrypts your data
Cyber threats have an enviable diversity and a proof of ingenuity of hackers is ransomware, a malware which encrypts your data in the “hard drive” and you can not regain access unless you pay an amount of money as a reward. Few threats act in a way so

NTP critical vulnerability, solved by OS X update
The myth which says that Apple’s operating system, OS X is more protected against hacker attacks than other operating systems was once again dismissed. A critical vulnerability that could affect Mac users proved so dangerous that led the Cupertino company to publish for the first time in

Focus on multidirectional malware and spyware on 2015
Dangerous malware such as Uroburos, spyware on Android smartphones and a growing number of cases involving malware attacks on mobile devices – 2014 was marked by cyber espionage, hacker attacks and cyber campaigns. Number of 3.5 million new strains of malware has been exceeded for the first

After hackers threats, Sony decided to cancel Christmas release of The Interview
US investigators have established that cyber attack on Sony Pictures was conducted by North Korea, according to official sources in Washington, film studio was forced to cancel the launch of the film “The Interview”, a decision widely criticized by Hollywood on Tuesday. A group of computer pirates who showed
