Two days ago I posted an article about a Facebook vulnerability that allows deleting any photo. The person who discovered the vulnerability said on it’s personal blog that Facebook payed him $12500 for reporting this vulnerability.
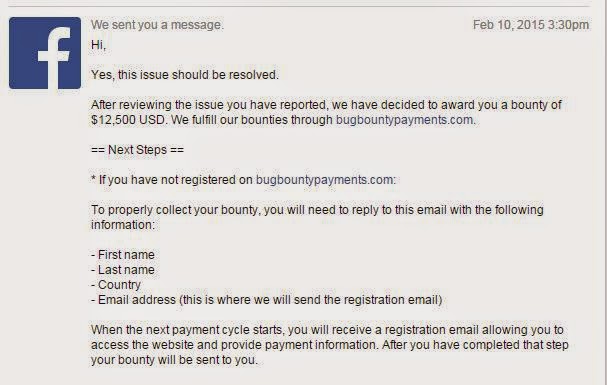
If you want to read about the vulnerability that Laxman Muthiyah discovered just follow this link: http://www.hackingnews.com/vulnerability/facebook-vulnerability-allows-deleting-photo/
But in this article I want to offer some information regarding Facebook’s Bug Bounty Program and also, some other tech companies such as Google, Microsoft, Yahoo, Twitter and more.
First of all, what is a bug bounty program?
According to wikipedia,
A bug bounty program is a deal offered by many website and software developers by which individuals can receive recognition and compensation for reporting bugs, especially those pertaining to exploits and vulnerabilities. These programs allow the developers to discover and resolve bugs before the general public is aware of them, preventing incidents of widespread abuse. Bug bounty programs have been implemented by Facebook, Yahoo!, and Google, among others.
How to find Bug Bounty programs?
1. HackerOne – https://hackerone.com/programs
2. Bugcrowd – https://bugcrowd.com/list-of-bug-bounty-programs
3. Bugsheet – http://www.bugsheet.com/bug-bounties
4. Microsoft Bug Bounty – https://technet.microsoft.com/en-us/library/dn425036.aspx
5. Google Bug Bounty – http://www.google.com/about/appsecurity/reward-program/
The most famous bug bounty website is HackerOne. This bounty program is primarily aimed at computer security experts who can highlight vulnerabilities that may impend on the development of web tools and applications. Hacker One is used by: Facebook, Dropbox, Vimeo, Sucuri, Twitter, WePay, CloudFlare, 99designs, Secret, Yahoo,
It comes with several conditions:
A critical flaw involving a large number of users,
A bug affecting several editors,
A bug affecting a publisher with a dominant position.
Bugcrowd was founded in 2012 by CEO Casey Ellis and CTO Chris Raethke to help level the vulnerability assessment playing field. By leveraging the economic, expertise, and sheer numbers of the crowd, the company is redefining the cybersecurity market.
It’s revolutionary approach to cybersecurity combines a proprietary vulnerability reporting platform with the largest crowd of security researchers on the planet.
Bugcrowd is used by lots of tech companies, such as: Facebook, Yahoo, Avast, Avira, 99designs, Blackberry, CPanel, Digital Ocean, Dropbox, eBay, Foursquare, Freelancer, Github, Google, HackerOne, Instagram and many more. You can find the whole list here: https://bugcrowd.com/list-of-bug-bounty-programs.
Bugsheet is just a list of the companies that offer bug bounty programs. On the bugsheet website you can find the page related to bug bounty programs for a lot of companies that use bug bounty programs. So this is the place to start searching for bug bounty programs.
What is the best payed vulnerability?
Companies pay for vulnerabilities a price between $50 and $15000. There are some exceptions when were discovered critical vulnerabilities and the companies offered 6 digit rewards.
The best payed domains are:
Remote code execution – google pay up to $20000
Unrestricted file system or database access – google pay up to $10000
Logic flaw bugs leaking or bypassing significant security controls – google pay up to $10000
Execute code on the client (eg: cross site scripting (known as XSS), code execution) – google pay up to $7500
Other valid security vulnerabilities (eg: cross site request forgery (known as CSRF), Clickjacking, Information Leak) – google pay up to $7500
According to Facebook, to qualify for a bounty, you must:
Adhere to our Responsible Disclosure Policy (above)
Be the first person to responsibly disclose the bug
Report a bug that could compromise the integrity of user data, circumvent the privacy protections of user data, or enable access to a system within our infrastructure, such as:
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF/XSRF)
Broken Authentication (including Facebook OAuth bugs)
Circumvention of our Platform/Privacy permission models
Remote Code Execution
Privilege Escalation
Provisioning Errors
Report a bug in Facebook or one of the following qualifying products or acquisitions:
Parse
Onavo
Oculus
Moves
osquery
Make every effort to use a test account instead of a real account when investigating bugs. When you are unable to reproduce a bug with a test account, it is acceptable to use a real account, except for automated testing.
Not interact with other accounts without the consent of their owners.
Not reside in a country under any current U.S. Sanctions (e.g., North Korea, Libya, Cuba, etc.)
The minimum reward that Facebook offers is $500. You can find more about Facebook bug bounty here.
Facebook’s Hall of Fame list can be found here: https://www.facebook.com/whitehat/thanks

