Security researcher Joshua J. Drake (@jduck) discovered one of the worst Android vulnerabilities discovered to date. This android critical vulnerability targets 95% of Android devices, almost 1 billion devices. Every Android phone or tablet with a version between 2.2 and 5.1 of the android operating system is vulnerable to this vulnerability.
How exactly does this android vulnerability works?
The attacker only needs to know the victim’s phone number. A text message can allow remote code execution. So almost all android users are vulnerable to this exploit. A sophisticated cyber attack can also delete the message before the victim see it. In this way, the victim will only see the notification of the received message.
On the Zimperium Mobile Security Blog, you can see a demonstration of this attack.
I created a screenshot of this mobile attack. The test device is a Nexus 5 with Android Lollipop 5.1.1. You can see the attack below:
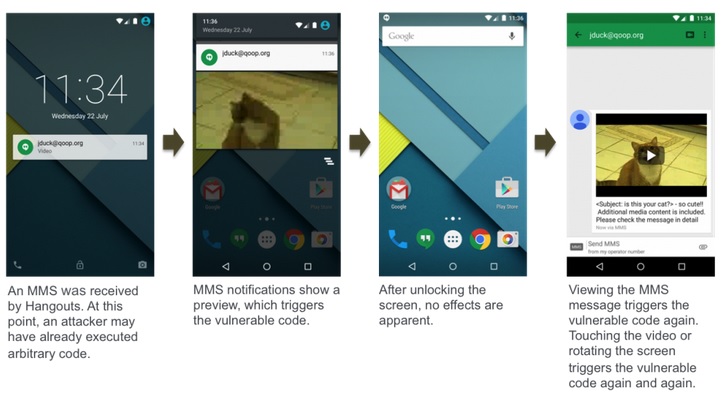
Image Credits – Zimperium Mobile Security Blog
How does this android attack technically works?
The hackers target an android library called Stagefright. Stagefright is a media library that processes several media formats. This library is written in C++ in order to consume less memory.
The Stagefright vulnerability was assigned with the following CVEs:
- CVE-2015-1538
- CVE-2015-1539
- CVE-2015-3824
- CVE-2015-3826
- CVE-2015-3827
- CVE-2015-3828
- CVE-2015-3829
Want to learn more about Android Security, Vulnerabilities and Penetration?
Want to get in touch with Joshua Drake?
Drake’s research will be presented at Black Hat USA on August 5 and DEF CON 23 on August 7. Join these hacking conferences in order to learn more about penetration testing, cyber crime and how to prevent being hacked. Doesn’t matter if it’s a mobile or a web application, you will see at these security conferences that there’s no unhackable application.

