security Archive

Superfish: Lenovo is only the tip of the iceberg
In Malware
Security experts from G Data SecurityLabs analyzed Superfish adware. In this process, analysts have encountered in program, a technology component, called SSL digestion. It uses a root certificate which is poorly secured and has extensive rights on the computer. SSL Digestor intercept safe HTTPS connections which can be decrypted.

Android phones can be tracked just with battery power alone
We all know that a phone uses more power the further away it is from a cell tower as it tries to connect. So, an Android phone can be tracked by studying their power use over time, without using their GPS or wi-fi/data usage. Extra power is used by

PwC: cyber attacks caused damage to companies estimated at 2.7 billion. dollars
Number of cyber security incidents detected in companies in 2014 increased by 48% over the previous year, reaching 42.8 million global events, apparent from an analysis performed by PwC – The Global State of Information Security Survey 2015, based on the responses of 9,700 managers responsible
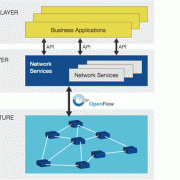
Software Defined Networking (SDN), the next Eldorado of IT
Few people know , SDN has everything it takes to become a new standard of IT. Basically, SDN brings a global expansion of virtualization from hardware and storage to further infrastructure networks. Thus, interventions on the networks will not require a manual configuration, a direct intervention
Forbes.com attacked by Chinese hackers
Chinese hackers attacked Forbes.com web site with an malicious software (malware) that target only certain visitors, which include several US defense institutions and financial services, according to cyber security companies, iSIGHT. According to iSIGHT and Invincea, someone compromised this application for three days (November 28 until December 1, 2014) or

Google warns Microsoft and Apple: fix the vulnerability or we will disclose
Google said that its elite team consisting of hackers and programmers search security deficiencies of its software applications and other companies, Google warning that if its competitors will not eliminate vulnerabilities within 90 days, then they will make public. Google claims that software vendors must act quickly

How it will look the new iPhone7 and what features will have
In Technology
Apple has not announced the release date for the new generation of iPhone, so the specialized press is plenty of room for speculation and scenarios. If Apple will launch iPhone representatives 6S, the new iPhone will have some improvements compared to the already out on the

Anthem, an insurance company, was the target of a large cyber attack
Anthem Insurance Company, the second largest in the United States, was the target of a cyber attack, hackers managed to steal personal data for many former or current clients and employees of the company, reports Reuters. Anthem announced Wednesday that hackers broke into an IT system

Cloud, a new era of innovation for personal data protection
In Malware
A sophisticated cryptographic algorithm prevents unwanted distribution of personal data, including credit card details. IBM researchers have recently announced their intention to develop a technology based on cloud platform that will help users, giving a better protection for their personal data, when they are online, including date of birth,

USBdriveby can take control of a computer in a few seconds
A few months ago was discovered a worrying vulnerability of standard USB which does not seem to be repaired, called BadUSB. Until now such information was only theoretical and no one has developed a software which can uses this security hole, but a well-known hacker Samy Kamkar has
