hacking Archive

How it will look the new iPhone7 and what features will have
In Technology
Apple has not announced the release date for the new generation of iPhone, so the specialized press is plenty of room for speculation and scenarios. If Apple will launch iPhone representatives 6S, the new iPhone will have some improvements compared to the already out on the

Anthem, an insurance company, was the target of a large cyber attack
Anthem Insurance Company, the second largest in the United States, was the target of a cyber attack, hackers managed to steal personal data for many former or current clients and employees of the company, reports Reuters. Anthem announced Wednesday that hackers broke into an IT system

Cloud, a new era of innovation for personal data protection
In Malware
A sophisticated cryptographic algorithm prevents unwanted distribution of personal data, including credit card details. IBM researchers have recently announced their intention to develop a technology based on cloud platform that will help users, giving a better protection for their personal data, when they are online, including date of birth,

USBdriveby can take control of a computer in a few seconds
A few months ago was discovered a worrying vulnerability of standard USB which does not seem to be repaired, called BadUSB. Until now such information was only theoretical and no one has developed a software which can uses this security hole, but a well-known hacker Samy Kamkar has

2014 Security News Review
In this article you’ll find the hottest hacking news from 2014. Below you’ll find the most important security news for each month of 2014. All titles are selected from our hacking news blog. We hope you enjoyed reading these news and we assure you that better quality
Facebook says it was not the victim of a cyber attack, invoking technical problems
Facebook says it was not the victim of a cyber attack, invoking technical problems this morning for unavailability. Facebook invoke technical issues related to configuration changes to systems which fall off 50 minutes this morning. “The network” denies rumors which says that it was the victim of a cyber
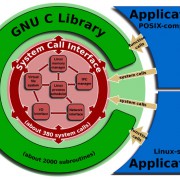
GHOST glibc vulnerability (CVE-2015-0235) affects Linux Machines
A critical vulnerability has been found in glibc, the GNU C library, that affects almost all Linux systems dating back to 2000. Attackers can use this flaw to execute code and remotely gain control of Linux machines. The Red Hat Product Security has been made aware of
CENTCOM Twitter and YouTube accounts, hacked by a terrorist group of Islamic State
An affiliated group of terrorist network of Islamic State has conducted cyber attacks against official Twitter and YouTube accounts of US Central Command (CENTCOM), broadcasting threats against US troops, reports The Washington Post newspaper. Assigned messages of hackers have begun to appear on the CENTCOM Twitter

IBM Study: Companies rethinking cyber security strategies
Approximately 60% of leaders in security believe that hackers have exceeded cybersecurity capabilities within their organization, said in a study conducted by IBM. Over 80% of security leaders believe that the challenges of external threats is increasing, while 60% agree that oraganizatiile are exceeded in this cyber war,

Blackhat 2015 – a new Hacking Movie Trailer
Storyline – A furloughed convict and his American and Chinese partners hunt a high-level cybercrime network from Chicago to Los Angeles to Hong Kong to Jakarta. Written by Morgan Davis Foehl and Michael Mann from a project Mann has been developing with Legendary for over a year,
